A group of Israeli researchers reckon they’ve cracked the challenge of crafting a reliable exploit for the Stagefright vulnerability that emerged in Android last year.
In a paper [PDF] that’s a cookbook on how to build the exploit for yourself, they suggest millions of unpatched Android devices are vulnerable to their design, which bypasses Android’s security defenses. Visiting a hacker’s webpage is enough to trigger a system compromise, we’re told.
Since no hot piece of infosec action exists without a name these days, the paper, written by Hanan Be’er of North-Bit, dubs the implementation of the Stagefright exploit “Metaphor.”
Stagefright is the name of a software library used by Android to parse videos and other media; it can be exploited by a booby-trapped message or webpage to execute malicious code on vulnerable devices.
The paper describes a three-step process to reliably hijacking an Android device:
The victim surfs to a malicious webpage that sends over a video file that crashes the operating system’s mediaserver software to reset its internal state. Some JavaScript on the page waits for mediaserver to restart, and then sends information about the device over the internet to the attacker’s private server.
This server then generates a custom video file that is sent to the device, which exploits Stagefright to reveal more information about the device’s internal state. This information is beamed back by the JavaScript to the attacker’s server, which uses the data to craft another video file that, when processed by Stagefright, starts executing a payload of malware embedded within the file on the victim’s handheld. This code runs with all the privileges it needs to spy on the device’s owner.
While North-Bit reckons its exploit design is reliable, you’ll have to, as described above, do some server-side work to deploy Metaphor.
In particular, you need to gather information about where libc.so and libicui8n.so are loaded in memory, and the jemalloc configuration in the device. This is why the aforementioned JavaScript phones home data about a victim’s device so the exploit can be tailored to attack the memory structures and firmware in that particular handset.
The exploit also needs a perform a heap spray to work, and that means the attacker may need to attempt exploitation multiple times on the target.
However, North-Bit says that with “further research it may be possible to lay aside all or some of the lookup tables” used to generate custom malicious video files – and that would lay the groundwork for a generic exploit.
The exploit specifically attacks the CVE-2015-3864 bug in a “fast, reliable and stealthy” way that bypasses ASLR – aka address space layout randomization, a mechanism that thwarts a lot of exploit writers.
It’s also important to note that the victim doesn’t have to press play on a rigged MPEG4 video file, because the bug is triggered when the web browser simply fetches and parses the file upon first seeing it.
“It was claimed [the bug] was impractical to exploit in the wild, mainly due to the implementation of exploit mitigations in newer Android versions, specifically ASLR,” the paper states.
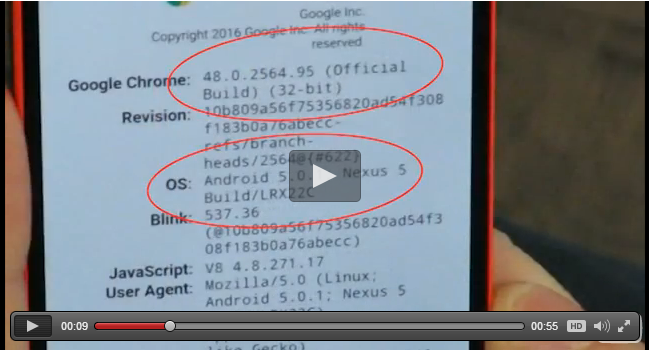
“The team here at North-Bit has built a working exploit affecting Android versions 2.2 to 4.0 and 5.0 to 5.1, while bypassing ASLR on versions 5.0 to 5.1 (as Android versions 2.2 to 4.0 do not implement ASLR).”
Google released security patches to kill Stagefright’s vulnerabilities, although not every Android phone and tablet can receive and install them: some manufacturers and network carriers were in no rush to update older models, leaving potentially millions of gadgets at the mercy of exploits like the one built by North-Bit.
Updated to add
A Google spokesman has been in touch to say: “Android devices with a security patch level of October 1, 2015 or greater are protected because of a fix we released for this issue (CVE-2015-3864) last year. As always, we appreciate the security community’s research efforts as they help further secure the Android ecosystem for everyone.”
Read the full post in The Register